We need first person technologies for the same reason we need first person voices: because there are some things only a person can say and do.
We need first person technologies for the same reason we need first person voices: because there are some things only a person can say and do.
Only a person can use the pronouns “I,” “me,” “my” and “mine.” Likewise, only a person can use tools such as screwdrivers, eyeglasses and pencils. Those things are all first person technologies. They were invented for individual persons to use.
We use first person technologies the same unique ways we use our voices. “The human voice is unmistakably genuine,” The Cluetrain Manifesto says. “It can’t be faked.” Same with first person technologies. GoPro cameras, for example, are first person technologies that are used as many different ways as the people who strap them to their helmets.
Here in the physical world, first person technologies are extensions of our bodies and our senses. When we swing a hammer, twist a fork, ride a bike and drive a car, our senses dwell within each of those things. They become part of us, and us part of them.
There are social influences on how we use first person technologies, of course, just as there are social influences on how we speak. But that does not diminish the personal nature of what we do with our tools and our voices. Each of us speaks, writes, walks and drives in ways that are ours alone.
What’s purely personal is clear in the physical world. In the networked world, however, it is not — and this is a problem that needs fixing.
For example, there was a time when personal computers were truly personal. They ran applications that you acquired (or created) and used by and for yourself. You did not have to subscribe to them as services, and they did not require some company’s cloud. That time was before personal computers became network nodes. We are in a new world now — one in which first person agency is both provided and limited by what the lawyers call second and third parties, out on the Net.
Take smartphones and tablets for example. These are personal in many intimate ways, but they are also suction cups on corporate tentacles. So, while you can still operate a PC as independently as you would a typewriter, you cannot operate your mobile device except by the graces of Apple, Google, Microsoft, Samsung and other controlling parties — especially your mobile network provider. And, unless you are a serious hacker, you can’t acquire apps except through company stores. Many of those apps are also just interfaces on remote services over which you have little control.
This state of things is one of the reasons why privacy has lately become a big issue. The term covers several concerns at once. Here is how Eben Moglen unpacks them:
Privacy—as we use the word in our conversations now all around the world, and particularly when we talk about the net— really means three things.
The first is secrecy, which our ability to keep messages “private,” so that their content is known only to those who we intend to receive them.
The second is anonymity, which is our ability to keep our messages—even when their content is open—obscure as to who has published them and who is receiving them. It is very important that anonymity is an interest we can have in both our publishing and our reading.
The third is autonomy, which is our ability to make our life decisions free any force which has violated our secrecy or our anonymity.
Our old PCs provided all of those graces. (So does your GoPro camera.) We have none of them with our smart mobile devices today. Not yet, anyway.
Books in the physical world are first person technologies as well. Digital ones we “buy” from Amazon are not, because they come with leashes. Eben asks, “What if every book for the last five hundred years had been reporting its readers at headquarters?”
We won’t get back our privacy, or make real progress toward real personal freedom, until we develop and deploy first person technologies for everybody. Without them our democracies and marketplaces will also continue to be compromised, because both require those three virtues of privacy.
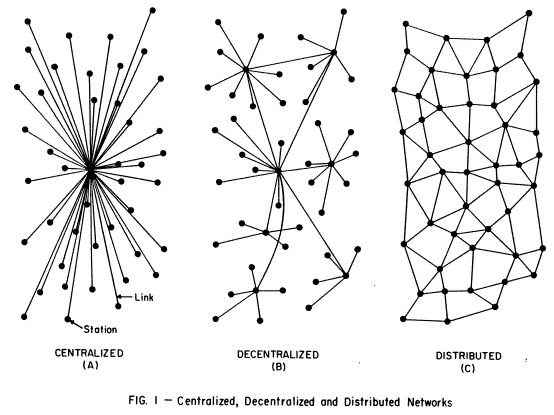
First person technologies are also required by the distributed design of the Net, which Paul Baran first describede in 1964, using this drawing:
The Internet is the one on the right. In it each node is equal and possesses full agency. It is also what Adriana Lukas calls a heterarchy. Routing (which Paul Baran called “hot potato” and we now call packet switching) takes the best available path, rather than running only through central (or multi-central) relay points. He posed this in contrast to the centralized model of computing, which prevailed at the time, and to decentralized networks, which reduced some of the risks of centralized networks but still held the same vulnerabilities, because they still contain central hubs and therefore also hierarchies. We experience those vulnerabilities today when services we depend on are attacked, and the privacy of many is compromised at once.
Design models and habits die long and hard, however; and it remains too easy to create centralized services, such as corporate clouds, and to deliver benefits from those that are good enough — until something goes wrong.
First person technologies are a step in the right direction: the distributed one.
From the start a variety of ProjectVRM developers have been developing first person technologies. Here’s a quick list:
- The Mine! Project
- webfinger
- AdblockPlus
- Disconnect
- Wickr
- telehash
- tent.io
- CloudOS
- KRL
- Mozilla Persona
- UMA — User Managed Access
- FinTP
- Open Mustard Seed and openPDS from IDCubed
- XDI and XDI for personal clouds
- Respect Trust Framework (promulgated by the Respect Network)
- Project Danube
- Freedom Box
- arkOS
- IndieBox (a personal cloud hardware project, and one of too many others to list from the Indie Web Camp)
Everything there is open source or uses open standards and protocols. There are many others I insult by not listing (corrections are invited); but the main thing is not just to give credit where due. It’s to show groundwork toward a whole new category: first person technology.
Nailing down what this category means, and contains, is job one. It isn’t easy, because there is plenty of gray in the networked world. But lines can and must be drawn. Here’s one: we can use them to make a dent in the universe. Here’s another: They move us from what Dave Winer describes as Model #1 to Model #2:
Once we’ve done that, we can see how first person technologies, for example, deliver benefits in all four of the development categories Fred Wilson listed in the speech he gave at LeWeb in December:
- Money
- Health and wellness
- Data leakage
- Trust and identity
Solutions here will come, like our own voices, from our sovereign and independent selves, using tools that extend our native capabilities. They won’t come only from systems others provide for us. They will, however, make those systems better as well.
Bonus link: Tahrir.