
 For as long as we’ve had economies, demand and supply have been attracted to each other like a pair of magnets. Ideally, they should match up evenly and produce good outcomes. But sometimes one side comes to dominate the other, with bad effects along with good ones. Such has been the case on the Web ever since it went commercial with the invention of the cookie in 1995, resulting in a calf-cow model in which the demand side — that’s you and me — plays the submissive role of mere “users,” who pretty much have to put up with whatever rules websites set on the supply side.
For as long as we’ve had economies, demand and supply have been attracted to each other like a pair of magnets. Ideally, they should match up evenly and produce good outcomes. But sometimes one side comes to dominate the other, with bad effects along with good ones. Such has been the case on the Web ever since it went commercial with the invention of the cookie in 1995, resulting in a calf-cow model in which the demand side — that’s you and me — plays the submissive role of mere “users,” who pretty much have to put up with whatever rules websites set on the supply side.
Consistent with Lord Acton’s axiom (“Power corrupts; absolute power corrupts absolutely”) the near absolute power of website cows over user calves has resulted in near-absolute corruption of website ethics in respect to personal privacy.
This has been a subject of productive obsession by Julia Anguin and her team of reporters at The Wall Street Journal, which have been producing the What They Know series (shortcut: http://wsj.com/wtk) since July 30, 2010, when Julia by-lined The Web’s New Gold Mine: Your Secrets. The next day I called that piece a turning point. And I still believe that.
Today came another one, again in the Journal, in Julia’s latest, titled Web Firms to Adopt ‘No Track’ Button. She begins,
A coalition of Internet giants including Google Inc. has agreed to support a do-not-track button to be embedded in most Web browsers—a move that the industry had been resisting for more than a year.
The reversal is being announced as part of the White House’s call for Congress to pass a “privacy bill of rights,” that will give people greater control over the personal data collected about them.
The long White House press release headline reads,
We Can’t Wait: Obama Administration Unveils Blueprint for a “Privacy Bill of Rights” to Protect Consumers Online
Internet Advertising Networks Announces Commitment to “Do-Not-Track” Technology to Allow Consumers to Control Online Tracking
Obviously, government and industry have been working together on this one. Which is good, as far as it goes. Toward that point, Julia adds,
The new do-not-track button isn’t going to stop all Web tracking. The companies have agreed to stop using the data about people’s Web browsing habits to customize ads, and have agreed not to use the data for employment, credit, health-care or insurance purposes. But the data can still be used for some purposes such as “market research” and “product development” and can still be obtained by law enforcement officers.
The do-not-track button also wouldn’t block companies such as Facebook Inc. from tracking their members through “Like” buttons and other functions.
“It’s a good start,” said Christopher Calabrese, legislative counsel at the American Civil Liberties Union. “But we want you to be able to not be tracked at all if you so choose.”
In the New York Times’ White House, Consumers in Mind, Offers Online Privacy Guidelines Edward Wyatt writes,
The framework for a new privacy code moves electronic commerce closer to a one-click, one-touch process by which users can tell Internet companies whether they want their online activity tracked.
Much remains to be done before consumers can click on a button in their Web browser to set their privacy standards. Congress will probably have to write legislation governing the collection and use of personal data, officials said, something that is unlikely to occur this year. And the companies that make browsers — Google, Microsoft, Apple and others — will have to agree to the new standards.
No they won’t. Buttons can be plug-ins to existing browsers. And work has already been done. VRM developers are on the case, and their ranks are growing. We have dozens of developers (at that last link) working on equipping both the demand and the supply side with tools for engaging as independent and respectful parties. In fact we already have a button that can say “Don’t track me,” plus much more — for both sides. Its calle the R-button, and it looks like this: ⊂ ⊃. (And yes, those symbols are real characters. Took a long time to find them, but they do exist.)
Yours — the user’s — is on the left. The website’s is on the right. On a browser it might look like this:
Underneath both those buttons can go many things, including preferences, policies, terms, offers, or anything else — on both sides. One of those terms can be “do not track me.” It might point to a fourth party (see explanations here and here) which, on behalf of the user or customer, maintains settings that control sharing of personal data, including the conditions that must be met. A number of development projects and companies are already on this case. All the above falls into a category we call EmanciTerm. Much has been happening as well around personal data stores (PDSes), also called “lockers,” “services” and “vaults.” These include:
Three of those are in the U.S., one in Austria, one in France, one in South Africa, and three in the U.K. (All helping drive the Midata project by the U.K. government, by the way.) And those are just companies with PDSes. There are many others working on allied technologies, standards, protocols and much more. They’re all just flying below media radar because media like to look at what big suppliers and governments are doing. Speaking of which… 🙂
Here’s Julia again:
Google is expected to enable do-not-track in its Chrome Web browser by the end of this year.
Susan Wojcicki, senior vice president of advertising at Google, said the company is pleased to join “a broad industry agreement to respect the ‘Do Not Track’ header in a consistent and meaningful way that offers users choice and clearly explained browser controls.”
White House Deputy Chief Technology Officer Daniel Weitzner said the do-not-track option should clear up confusion among consumers who “think they are expressing a preference and it ends up, for a set of technical reasons, that they are not.”
Some critics said the industry’s move could throw a wrench in a separate year-long effort by the World Wide Web consortium to set an international standard for do-not-track. But Mr. Ingis said he hopes the consortium could “build off of” the industry’s approach.
So here’s an invitation to the White House, Google, the 3wC, interested BigCos (including CRM companies), developers of all sizes and journalists who are interested in building out genuine and cooperative relationships between demand and supply::::
Join us at IIW — the Internet Identity Workshop — in Mountain View, May 1-3. This is the unconference where developers and other helpful parties gather to talk things over and move development forward. No speakers, no panels, no BS. Just good conversation and productive work. It’s our fourteenth one, and they’ve all been highly productive.
As for the r-button, take it and run with it. It’s there for the development. It’s meaningful. We’re past square one. We’d love to have all the participation we can get, from the big guys as well as the little ones listed above and here.
To help get your thinking started, visit this presentation of one r-button scenario, by Adam Marcus of MIT. Here’s another view of the same work, which came of of a Google Summer of Code project through ProjectVRM and the Berkman Center:

(Props to Oshani Seneviratne and David Karger, also both of MIT, and Ahmad Bakhiet, of Kings College London, for work on that project.)
If we leave fixing the calf-cow problem entirely up to the BigCos and BigGov, it won’t get fixed. We have to work from the demand side as well. In economies, customers are the 100%.
Here are some other stories, mostly gathered by Zemanta:
All look at the symptoms, and supply-side cures. Time for the demand side to demand answers from itself. Fortunately, we’ve been listening, and the answers are coming.
Oh, and by the way, Mozilla has been offering “do not track” for a long time. Other tools are also available:




 The idea is to start getting real about what we’re all doing and not doing.
The idea is to start getting real about what we’re all doing and not doing.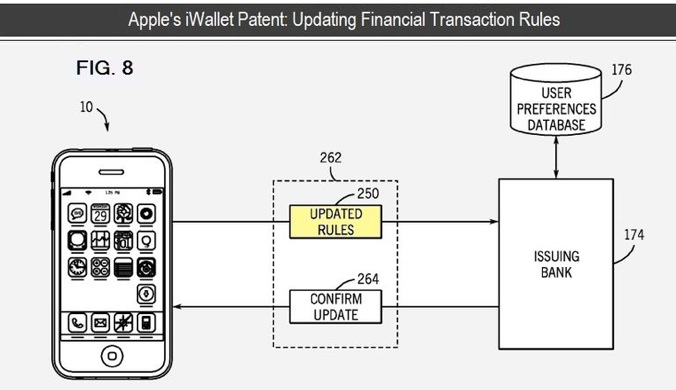



 For as long as we’ve had economies, demand and supply have been attracted to each other like a pair of magnets. Ideally, they should match up evenly and produce good outcomes. But sometimes one side comes to dominate the other, with bad effects along with good ones. Such has been the case on the Web ever since it went commercial with the invention of the cookie in 1995, resulting in a
For as long as we’ve had economies, demand and supply have been attracted to each other like a pair of magnets. Ideally, they should match up evenly and produce good outcomes. But sometimes one side comes to dominate the other, with bad effects along with good ones. Such has been the case on the Web ever since it went commercial with the invention of the cookie in 1995, resulting in a 

 Code talks, talk walks,
Code talks, talk walks,