This is from a December 2009 newsletter called Suitwatch, which I wrote for Linux Journal, and was 404’d long ago. (But I kept the original.) I’m re-posting it here because I think syndication may be the most potent power any of us have in the Internet age—and because the really simple kind, RSS, has been with us since before I wrote this piece. (I also think RSS has VRM implications as well, but I’ll leave those for another post.) My only edits here were to remove arcana and anachronisms that are pointless today. This graphic illustrates how entrenched and widespread RSS already is:
Until recently, the verb “syndication” was something big publishers and agencies did. As a kid, I recognized “© King Features Syndicate” was the one unfunny thing about Blondie or Dennis the Menace. All it meant to me was that some kind of Business was going on here.
Now millions of individual writers syndicate their own work, usually through RSS (Really Simple Syndication). Publishers and other large organizations do too. This article is syndicated. So are updates to product manuals, changes to development wikis, updates on SourceForge, and searches of keywords. You name it: if there’s something that updates frequently on the Web, there’s a better chance every minute that the new stuff is syndicated if it isn’t already.
Far as I know, not many sources are making money with it. Lots, however, are making money because of it. The syndicated world may not look like an economy yet. But trust me, it is.
At this early stage in its long future history, syndication is primarily a feature of blogging, which is primarily the product of too many people to count. Blogging is not about large-scale things. It’s about human beings who have no scale other than themselves. Only you can be good at being you, and nobody else is the same as you. Syndication does more to expand individual human potential than anything since the invention of type. Or perhaps ever. The syndicated world economy is the one that grows around unleashed personal powers of expression, productivity, creation, distribution, instruction, influence, leadership, whatever.
In a loose sense, syndication is one side of the conversation. Think about conversation in the best sense of the word: as the way people teach and learn from each other, the way topics start and move along. Syndication makes that happen in huge ways.
The notion that “markets are conversation”, popularized by The Cluetrain Manifesto, was borrowed from this case I used to make for a form of marketing that was far more natural and powerful than the formal kind:
- Markets are conversation, and
- Conversation is fire. Therefore,
- Marketing is arson.
If you want to set fires, start conversations that tend to keep going. Nothing does the latter better than syndication.
There are three reasons why we still don’t hear as much about syndication as we should (and will). First, it’s still new. Second, it didn’t come from The Big Guys. (It came from Dave Winer, father of RSS — Really Simple Syndication.) Third, it points toward a value system not grounded only in exchange — one especially suited for the Net, a deeply ironic worldwide environment where everybody is zero distance apart.
But let’s park the value system until later and talk about next week. That’s when I’ll be in San Francisco for Syndicate. It’s the second in a series of conferences by that name. The first was in New York last Spring.
Since I’m the conference chair (disclosure: it’s a paying gig), and since I’ll be giving both the introductory talk and the closing keynote, Syndication is on the front burner of my mind’s stove.
There are others subjects there as well, some of which will be visited in sessions at the show. RSS, for starters. And tagging—a practice so new it’s not even close to having standards of the sort we find at OASIS, the IETF, and the W3C. Instead, it has emerging standards, like the ones we find at microformats.org.
Like syndication, tagging is a long-tail activity. Something individuals do. Along with blogging and syndication, it helps outline a new branch of the Net we’re starting to call the Live Web — as opposed to the Static Web with “sites” that are “built” and tend not to change.
The World Live Web is the title of my December Linux For Suits column in Linux Journal. In it, I note that the directoryless nature of everything on the Web falls in the Unix file path east of the domain name. Every path to a document (or whatever) is a piece of straw in the static Web’s haystack. Google and Yahoo help us find needles in that haystack, but their amazing success at search also tends to confirm the haystack nature of the Static Web itself.
The Live Web is no less webby than the Static Web. They’re both parts of the same big thing. But the Live Web is new and very different. It cannot be understood in Static Web terms.
In that piece, I also observed that blogs, as continuing projects by human authors, leave chronological trails. These give the Live Web something of a structure: a chronological one that goes /year/month/day/date/post, even if that’s not the way each post’s URL is composed. There is an implicit organizational structure here, and it’s chronological.
Tagging, by which individuals can assign categorical tags of their own to everything from links to bookmarks to photos, has given the Live Web an ad hoc categorical structure as well.
So that’s what we’re starting to see emerge here: chronology and category. Rudimentary, sure, but real. And significant.
But not organized. New practices, and new ideas, are coming along too fast.
What matters, above all, is user-in-charge: a form of personal agency in the connected world. That’s a concept so key to everything else that’s happening on the Web, even on the Static one, that we may need a new word for it.
Or an old one, like independence, liberty, sovereignty, or autonomy. That’s my inner Libertarian, choosing those. If your sensibilities run a bit more to the social side, you may prefer words like actualization or fulfillment. Point is, the Big Boys aren’t in charge anymore. You are. I am. We are.
There’s an economy that will grow around us. I think free software and open-source practices (see various books and essays by Richard M. Stallman and Eric S. Raymond) put tracks in the snow that point in the direction we’re heading, but the phenomenon is bigger than that.
It’s also bigger than Google and Yahoo and Microsoft and IBM and Sun and Red Hat and Apple and the rest of the companies people (especially the media) look to for Leadership. For all the good those companies do in the world, the power shift is underway and is as certain as tomorrow’s dawn. The Big Boys will need to take advantage of it. We’ll need them to, as well.
This power shift is what I’d like to put in front of people’s attention when they come to Syndicate next week, or when they follow the proceedings in blogs and other reports.
Now more than ever, power is personal. Companies large and small will succeed by taking advantage of that fact. And by watching developments that aren’t just coming from The Usual Suspects. Including the Usual Economic Theories.
For example, not everything in an economy is about exchange, or the value chain, or about trade-offs of this for that. Many values come out of effort and care made without expectation of return. Consider your love for your parents, spouses, children, friends, and good work. Consider what you give and still get to keep. Consider debts erased by forgiveness. Consider how knowledge grows without its loss by anyone else.
Sayo Ajiboye, the Nigerian minister who so blew my mind in conversations we had on a plane nearly five years ago (Google them up if you like), taught me that markets are relationships, and not just conversations. Relationships, he said, are not just about exchange. They cannot be reduced to transactions. If you try, you demean the relationships themselves.
Also, in spite of the economic framings of our talk about morality and justice (owing favors, paying for crimes, just desserts), there is a deeper moral system that cannot be understood in terms of exchange. In fact, when you bring up exchange, you miss the whole thing. (Many great teachers have tried in futility to make this point, and I’m probably not doing any better.) Whatever it is, its results are positive. Growth in one place is not matched by shrinking in another. Value in both systems is created. But in the latter one, the purpose is not always, or exclusively, exchange, or profit. At least not from the activity itself. There are because effects at work. And we’re only beginning to understand them, much less practice them in new ways.
Toward that end, some questions…
Where did the Static Web, much less the Live Web, come from? What is it for? What are we doing with it? Whatever the answers, nothing was exchanged for them. (No, not even the record industry, the losses of which owe to their own unwillingness to take advantage of new opportunities opened by the Net.)
Nor was anything exchanged for Linux, which has grown enormously.
As Greg Kroah-Hartman said recently on the Linux-Elitists list,
Remember, Linux is a species, and we aren’t fighting anyone here, we are merely evolving around everyone else, until they aren’t left standing because the whole ecosystem changed without them realizing it.
Yes, we have living ends.


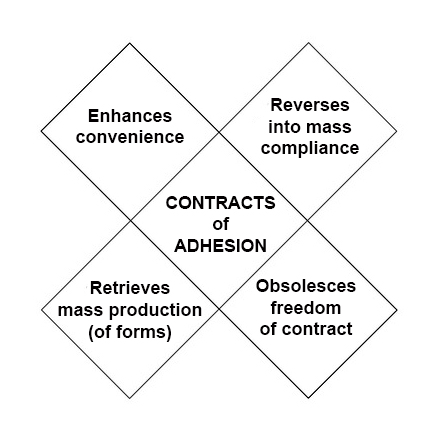
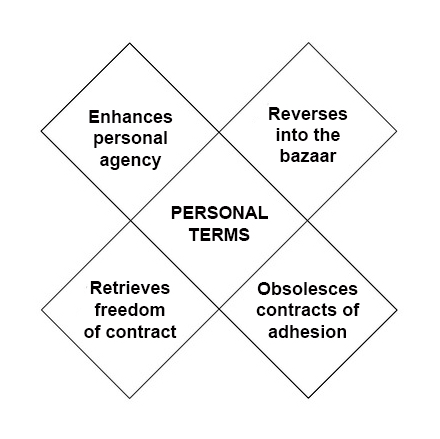
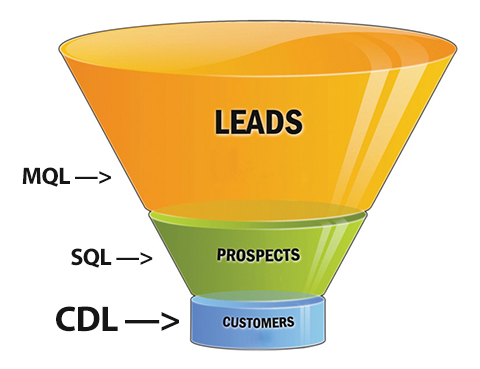 Imagine customers diving, on their own, straight down to the bottom of the sales funnel.
Imagine customers diving, on their own, straight down to the bottom of the sales funnel.

 Meerkat
Meerkat Periscope
Periscope