This is a shopping vs. advertising story that starts with the JBP Flip 2 portable speaker I bought last year, when Radio Shack was going bankrupt and unloading gear in “Everything Must Go!” sales. I got it half-off for $50, choosing it over competing units on the same half-bare shelves, mostly because of the JBL name, which I’ve respected for decades. Before that I’d never even listened to one.
This is a shopping vs. advertising story that starts with the JBP Flip 2 portable speaker I bought last year, when Radio Shack was going bankrupt and unloading gear in “Everything Must Go!” sales. I got it half-off for $50, choosing it over competing units on the same half-bare shelves, mostly because of the JBL name, which I’ve respected for decades. Before that I’d never even listened to one.
The battery life wasn’t great, but the sound it produced was much better than anything my laptop, phone or tablet put out. It was also small, about the size of a beer can, so I could easily take it with me on the road. Which I did. A lot.
Alas, like too many other small devices, the Flip 2’s power jack was USB micro-b. That’s the tiny flat one that all but requires a magnifying glass to see which side is up, and tends to damage the socket if you don’t slip it in exactly right, or if you force it somehow. While micro-b jacks are all design-flawed that way, the one in my Flip 2 was so awful that it took great concentration to make sure the plug jacked in without buggering the socket.
Which happened anyway. One day, at an AirBnB in Maine, the Flip 2’s USB socket finally failed. The charger cable would fit into the socket, but the socket was loose, and the speaker wouldn’t take a charge. After efforts at resuscitation failed, I declared the Flip 2 dead.
But I was still open to buying another one. So, to replace it, I did what most of us do: I went to Amazon. Naturally, there were plenty of choices, including JBL Flip 2s and newer Flip 3s, at attractive prices. But Consumer Reports told me the best of the bunch was the Bose Soundlink Color, for $116.
So I bought a white Bose, because my wife liked that better than the red JBL.
The Bose filled Consumer Reports’ promise. While it isn’t stereo, it sounds much better than the JBL (voice quality and bass notes are remarkable). It’s also about the same size (though with a boxy rather than a cylindrical shape), has better battery life, and a better user interface. I hate that it charges through a micro-b jack, but at least this one is easier to plug and unplug than the Flip 2 had been. So that story had a happy beginning, at least for me and Bose.
It was not happy, however, for me and Amazon.
Remember when Amazon product pages were no longer than they needed to be? Those days are gone. Now pages for every product seem to get longer and longer, and can take forever to load. Worse, Amazon’s index page is now encrusted with promotional jive. Seems like nearly everything “above the fold” (before you scroll down) is now a promo for Amazon Fashion, the latest Kindle, Amazon Prime, or the company credit card—plus rows of stuff “inspired by your shopping trends” and “related to items you’ve viewed.”
But at least that stuff risks being useful. What happens when you leave the site, however, isn’t. That’s because, unless you’re running an ad blocker or tracking protection, Amazon ads for stuff you just viewed, or put in your shopping cart, follow you from one ad-supported site to another, barking at you like a crazed dog. For example:

I lost count of how many times, and in how many places, I saw this Amazon ad, or one like it, for one speaker, the other, or both, after I finished shopping and put the Bose speaker in my cart.
Why would Amazon advertise something at me that I’ve already bought, along with a competing product I obviously chose not to buy? Why would Amazon think it’s okay to follow me around when I’m not in their store? And why would they think that kind of harassment is required, or even okay, especially when the target has been a devoted customer for more than two decades, and sure to return and buy all kinds of stuff anyway? Jeez, they have my business!
And why would they go out of their way to appear both stupid and robotic?
The answers, whatever they are, are sure to be both fully rationalized and psychotic, meaning disconnected from reality, which is the marketplace where real customers live, and get pissed off.
And Amazon is hardly alone at this. In fact the practice is so common that it became an Onion story in October 2018: Woman Stalked Across 8 Websites By Obsessed Shoe Advertisement.
The ad industry’s calls this kind of stalking “retargeting,” and it is the most obvious evidence that we are being tracked on the Net. The manners behind this are completely at odds with those in the physical world, where no store would place a tracking beacon on your body and use it to follow you everywhere you go after you leave. But doing exactly that is pro forma for marketing in the digital world.
When you click on that little triangular symbol in the corner of the ad, you can see how the “interactive” wing of the advertising business, generally called adtech, rationalizes surveillance:
 The program is called AdChoices, and it’s a creation of those entities in the lower right corner. The delusional conceits behind AdChoices are many:
The program is called AdChoices, and it’s a creation of those entities in the lower right corner. The delusional conceits behind AdChoices are many:
- That Ad Choices is “yours.” It’s not. It’s theirs.
- That “right ads” exist, and that we want them to find us, at all times.
- That making the choices they provide actually gives us control of advertising online.
- That our personal agency—the power to act with full effect in the world—is a grace of marketers, and not of our own independent selves.
Not long after I did that little bit of shopping on Amazon, I also did a friend the favor of looking for clothes washers, since the one in her basement crapped out and she’s one of those few people who don’t use the Internet and never will. Again I consulted Consumer Reports, which recommended a certain LG washer in my friend’s price range. I looked for it on the Web and found the best price was at Home Depot. So I told her about it, and that was that.
For me that should have been the end of it. But it wasn’t, because now I was being followed by Home Depot ads for the same LG washer and other products I wasn’t going to buy, from Home Depot or anybody else. Here’s one:
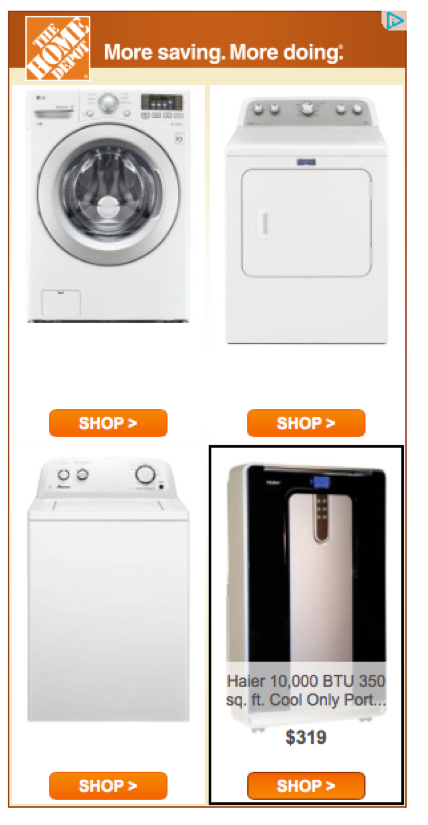
Needless to say, this didn’t endear me to Home Depot, to LG, or to any of the sites where I got hit with these ads.
All these parties failed not only in their mission to sell me something, but to enhance their own brands. Instead they subtracted value for everybody in the supply chain of unwelcome tracking and unwanted message targeting. They also explain (as Don Marti does here) why ad blocking has grown exactly in pace with growth in retargeting.
I subjected myself to all this by experimentally turning off tracking protection and ad blockers on one of my browsers, so I could see how the commercial Web works for the shrinking percentage of people who don’t protect themselves from this kind of abuse. I do a lot of that, as part of my work with ProjectVRM. I also experiment a lot with different kinds of tracking protection and ad blocking, because the developers of those tools are encouraged by that same work here.
For those new to the project, VRM stands for Vendor Relationship Management, the customer-side counterpart of Customer Relationship Management, the many-$billion business by which companies manage their dealings with customers—or try to.
Our purpose with ProjectVRM is to encourage development of tools that give us both independence from the companies we engage with, and better ways of engaging than CRM alone provides: ways of engaging that we own, and are under our control. And relate to the CRM systems of the world as well. Our goal is VRM+CRM, not VRM vs. CRM.
Ad blocking and tracking protection are today at the leading edge of VRM development, because they are popular and give us independence. Engagement, however, isn’t here yet—at least not at the same level of popularity. And it probably won’t get here until we finish curing business of the brain cancer that adtech has become.
[Later…] After reading this, a friend familiar with the adtech business told me he was sure Bose’s and JPL’s agencies paid Amazon’s system for showing ads to “qualified leads,” and that Amazon’s system preferred to call me a qualified lead rather than a customer whose purchase of a Bose speaker (from Amazon!) mattered less than the fact that its advertising system could now call me a qualified lead. In other words, Amazon was, in a way, screwing Bose and JPL. If anyone has hard facts about this, please send them along. Until then I’ll consider this worth sharing but still unproven.











 This is a shopping vs. advertising story that starts with the JBP Flip 2 portable speaker I bought last year, when Radio Shack was going bankrupt and unloading gear in “Everything Must Go!” sales. I got it half-off for $50, choosing it over competing units on the same half-bare shelves, mostly because of the JBL name, which I’ve respected for decades. Before that I’d never even listened to one.
This is a shopping vs. advertising story that starts with the JBP Flip 2 portable speaker I bought last year, when Radio Shack was going bankrupt and unloading gear in “Everything Must Go!” sales. I got it half-off for $50, choosing it over competing units on the same half-bare shelves, mostly because of the JBL name, which I’ve respected for decades. Before that I’d never even listened to one.
 The program is called
The program is called 

 Meerkat
Meerkat Periscope
Periscope