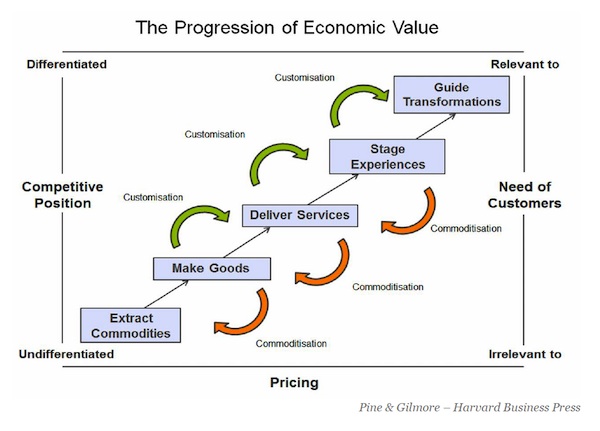
Here’s a picture that’s worth more than a thousand words:

He’s with MAIF, the French insurance company, speaking at MyData 2016 in Helsinki, a little over a month ago. Here’s another:

That’s Sean Bohan, head of our steering committee, expanding on what many people at the conference already knew.
I was there too, giving the morning keynote on Day 2:
It was an entirely new talk. Pretty good one too, especially since I came up with it the night before.
See, by the end of Day 1, it was clear that pretty much everybody at the conference already knew how market power was shifting from centralized industries to distributed individuals and groups (including many inside centralized industries). It was also clear that most of the hundreds of people at the conference were also familiar with VRM as a market category. I didn’t need to talk about that stuff anymore. At least not in Europe, where most of the VRM action is.
So, after a very long journey, we’re finally getting started.
In my own case, the journey began when I saw the Internet coming, back in the ’80s. It was clear to me that the Net would change the world radically, once it allowed commercial activity to flow over its pipes. That floodgate opened on April 30, 1995. Not long after that, I joined the fray as an editor for Linux Journal (where I still am, by the way, more than 20 years later). Then, in 1999, I co-wrote The Cluetrain Manifesto, which delivered this “one clue” above its list of 95 Theses:

And then, one decade ago last month, I started ProjectVRM, because that clue wasn’t yet true. Our reach did not exceed the grasp of marketers in the world. If anything, the Net extended marketers’ grasp a lot more than it did ours. (Shoshana Zuboff says their grasp has metastasized into surveillance capitalism. ) In respect to Gibson’s Law, Cluetrain proclaimed an arrived future that was not yet distributed. Our job was to distribute it.
Which we have. And we can start to see results such as those above. So let’s call Phase One a done thing. And start thinking about Phase Two, whatever it will be.
To get that work rolling, here are a few summary facts about ProjectVRM and related efforts.
First, the project itself could hardly be more lightweight, at least administratively. It consists of:
- A mailing list with more than 600 members
- This blog
- A wiki with a lot of stuff in it, including concepts that are now starting to play out in different ways. In addition to VRM itself, these include intentcasting, EmanciPay and the r-button.
- Gatherings twice a year at the Computer History Museum in Silicon Valley. These are VRM Day and the Internet Identity Workshop, or IIW. (The next ones are coming up later this month. You’re all invited.)
Second, we have a spin-off: Customer Commons, which will do for personal terms of engagement (one each of us can assert online) what Creative Commons (another Berkman-Klein spinoff) did for copyright.
Third, we have a list of many dozens of developers, which seem to be concentrated in Europe and Australia/New Zealand. Two reasons for that, both speculative:
- Privacy. The concept is much more highly sensitive and evolved in Europe than in the U.S. The reason we most often get goes, “Some of our governments once kept detailed records of people, and those records were used to track down and kill many of them.” There are also more evolved laws respecting privacy. In Australia there have been privacy laws for several years requiring those collecting data about individuals to make it available to them, in forms the individual specifies. And in Europe there is the General Data Protection Regulation, which will impose severe penalties for unwelcome data gathering from individuals, starting in 2018.
- Enlightened investment. Meaning investors who want a startup to make a positive difference in the world, and not just give them a unicorn to ride out some exit. (Which seems to have become the default model in the U.S., especially Silicon Valley.)
What we lack is research. And by we I mean the world, and not just ProjectVRM.
Research is normally the first duty of a project at the Berkman Klein Center, which is chartered as a research organization. Research was ProjectVRM’s last duty, however, because we had nothing to research at first. Or, frankly, until now. That’s why we were defined as a development & research project rather than the reverse.
Where and how research on VRM and related efforts happens is a wide-open question. What matters is that it needs to be done, starting soon, while the “before” state still prevails in most of the world, and the future is still on its way in delivery trucks. Who does that research matters far less than the research itself.
So we are poised at a transitional point now. Let the conversations about Phase Two commence.



 In
In 







 It’s a simple QR code, like the one on the right. The pioneering company here is
It’s a simple QR code, like the one on the right. The pioneering company here is