A few minutes ago, on a mailing list, somebody asked me if Google hadn’t shown people don’t mind having personal data harvested as long as they get value in exchange for it. Here’s what I answered:
It’s not about Google — or Google alone. It’s about the wanton and widespread harvesting of personal data without permission, by pretty much the entire digital marketing field, or what it has become while in maximum thrall of Big Data.
That this is normative in the extreme does not make it right, or even sustainable. The market — customers like you and me — doesn’t like it. Technologists, sooner or later, will provide customers with means of control they still lack today.
The plain fact is that most people don’t like surveillance-based marketing. Study after study (by TRUSTe, Pew, Customer Commons and others) have shown that 90+% of people have problems with the way their data and their privacy are abused online.
“The Tradeoff Fallacy: How Marketers Are Misrepresenting American Consumers and Opening Them Up to Exploitation” by Annenberg (at the U. of Pa) says,
a majority of Americans are resigned to giving up their data—and that is why many appear to be engaging in tradeoffs. Resignation occurs when a person believes an undesirable outcome is inevitable and feels powerless to stop it. Rather than feeling able to make choices, Americans believe it is futile to manage what companies can learn about them. The study reveals that more than half do not want to lose control over their information but also believe this loss of control has already happened.
More from Penn News:
Survey respondents were asked whether they would accept “tradeoffs,” such as discounts, in exchange for allowing their supermarkets to collect information about their grocery purchases. Among the key findings:
• 91 percent disagree (77 percent of them strongly) that “if companies give me a discount, it is a fair exchange for them to collect information about me without my knowing.”
• 71 percent disagree (53 percent of them strongly) that “it’s fair for an online or physical store to monitor what I’m doing online when I’m there, in exchange for letting me use the store’s wireless Internet, or Wi-Fi, without charge.”
• 55 percent disagree (38 percent of them strongly) that “it’s okay if a store where I shop uses information it has about me to create a picture of me that improves the services they provide for me.”
Only about 4 percent agree or agree strongly with all three propositions.
But 58 percent agreed with both of the following two statements that together indicate resignation: “I want to have control over what marketers know about me online” and “I’ve come to accept that I have little control over what marketers can learn about me online.”
The Net we know today was born only twenty years ago, when it opened to commercial activity. We are still naked there, lacking in clothing and shelter (to name two familiar privacy technologies in the physical world). Eventually we’ll have clothing and shelter in many forms, good means for preventing and permitting the ways others deal with us, and full agency in our dealings with business and government.
In the meantime we’ll have a status quo to which we remain resigned.
I suspect that even Google knows this will change.
Bonus Link.
Think about an irony here. Most brick-and-mortar merchants would be appalled at the thought of placing tracking beacons on visiting customers, to spy on them after they leave the store, just so they can be “delivered” a better “advertising experience.” And obviously, customers would hate it too. Yet many of the same merchants hardly think twice about doing the same online.
This will change because there is clear market sentiment against it. We see this through pressure toward regulation (especially in Europe), and through ad and tracking blocking rates that steadily increase.
But both regulation and blockers are stone tools. Eventually we’ll get real clothing and shelter.
That’s what we’ve been working on here with ProjectVRM. It’s taking longer than we expected at first, but it will happen, and not just because there is already a lot of VRM development going on.
It will happen because we have the Net, and the Net is not just Google and Facebook and other modern industrial giants. The Net is where all of those companies live, in the company of customers, to whom, — sooner or later, they become accountable.
Right now marketing is not taking the massive negative externalities of surveillance into account, mostly because marketing is a B2B rather than a B2C business, and there persists a blindered mania around Big Data. But they will take those externalities into account eventually, because the Cs of the world will gain the power to protect themselves against unwanted surveillance, and will provide far more useful economic signaling to the businesses of the world than marketing can ever guess at.
Once that happens, the surveillance marketing business, and what feeds it, will collapse.
“A house divided against itself cannot stand,” Lincoln said. That was in 1858, and in respect to slavery. In 2015 the language of marketing — in which customers are “targets” to be “acquired,” “controlled,” “managed” and “locked in” — is not much different than the language of slave owners in Lincoln’s time.
This will change for the simple reason that we are not slaves. We are the ones with the money, the choice about patronage, and the network. Companies that give us full respect will be the winners in the long run. Companies that continue to treat us as less than human will suffer the consequences.
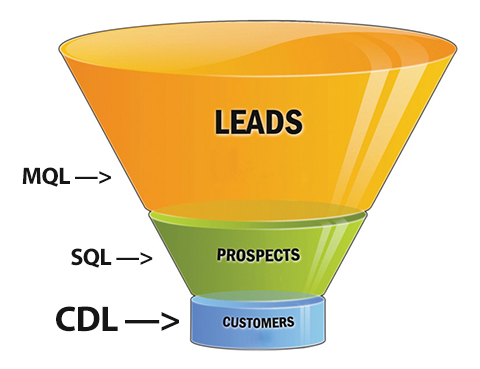 Imagine customers diving, on their own, straight down to the bottom of the sales funnel.
Imagine customers diving, on their own, straight down to the bottom of the sales funnel.




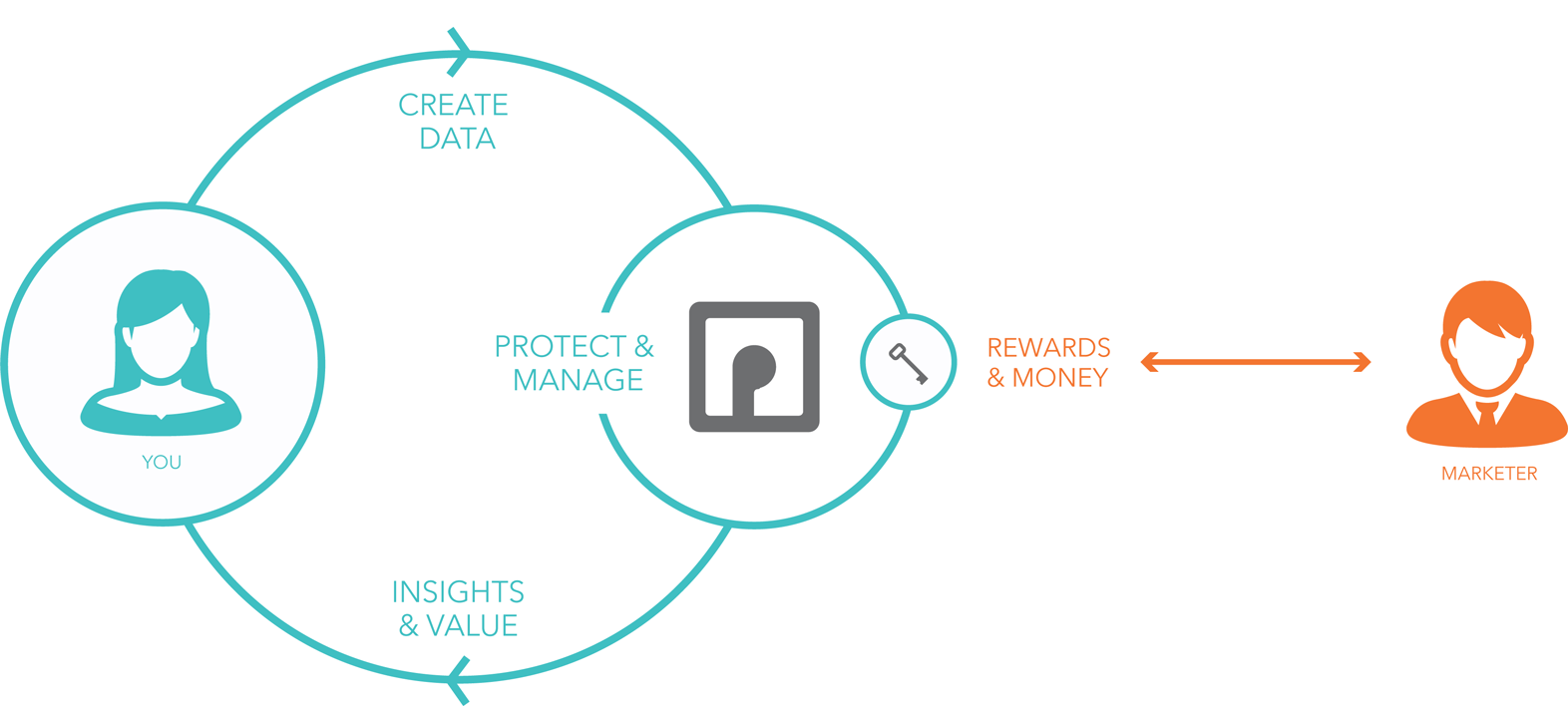
 In
In